A tech expert has broken down ‘clues’ within a sophisticated phishing email which has been sent to Gmail users from a ‘valid, signed email’.
Founder of Ethereum Name Service, Nick Johnson, took to Twitter last month to raise awareness of ‘an extremely sophisticated phishing attack’ explaining it ‘exploits a vulnerability in Google’s infrastructure’.
And given cybersecurity company Kaspersky shared an article about it last week, it would seem the attack is ongoing – UNILAD has contacted Google for comment.
Johnson took to Twitter on April 16 to share screenshots of the email he received, analysing the images explaining just how advanced the phishing attack is.


Have you received an email from no-reply@google.com? (Illustration by Mateusz Slodkowski/SOPA Images/LightRocket via Getty Images)
What does the ‘no-reply’ phishing email looks like?
The ‘first thing to note’? A ‘valid, signed email’.
“It really was sent from no-reply@google.com,” he explains. “It passes the DKIM signature check, and GMail displays it without any warnings – it even puts it in the same conversation as other, legitimate security alerts.”
Not only this, but the ‘Sites link’ then takes you to ‘a very convincing ‘support portal’ page’, which has a domain which looks ‘legit’ too.
Should you then click on ‘Upload additional documents’ or ‘View case’, you’d also be taken to a ‘signin page’ which is ‘an exact duplicate of the real thing’.
“The only hint it’s a phish is that it’s hosted on http://sites.google.com instead of http://accounts.google.com,” he adds.
Johnson theorized the scam works in ‘harvest[ing] your login credentials’ should you put them in and then ‘use them to compromise your account’.
Unsurprisingly, he didn’t go further to check.
But how was the phishing attack able to make itself look so believable?


The phishing email is seriously advanced (Twitter/ @nicksdjohnson)
How does the phishing ‘no-reply’ email look so ‘convincing’?
Essentially, the phishers register a domain, create a Google account for ‘me@domain’ and then create a Google OAuth application where they enter the Phishing message alongside some whitespace and ‘Google Legal Support’.
“Now they grant their OAuth app access to their ‘me@…’ Google account. This generates a ‘Security Alert’ message from Google, sent to their ‘me@…’ email address. Since Google generated the email, it’s signed with a valid DKIM key and passes all the checks,” Johnson explains.
The scammers then ‘forward the message to their victims’ and ‘because DKIM only verifies the message and its headers and not the envelope, the message passes signature validation and shows up as a legitimate message in the user’s inbox – even in the same thread as legit security alerts’.
“Because they named their Google account ‘me@’, GMail shows the message was sent to ‘me’ at the top, which is the shorthand it uses when a message is addressed to your email address – avoiding another indication that might send up red flags,” he resolves.
And how this is possible? Well, Johnson argues it’s down to ‘two vulnerabilities in Google’s infra[structure]’.


The email was ‘really sent from no-reply@google.com‘ (Twitter/ @nicksdjohnson)
The ‘two vulnerabilities in Google infrastructure’
Johnson explains the ‘fake portal is fairly straightforward’ as users can ‘host content on a http://google.com subdomain’.
Johnson says there’s ‘no way to report abuse from the Sites interface too’, meaning it’s easier for the phishers to simply upload new versions of ‘arbitrary scrips and embeds’.
Johnson recommends Google ‘disable scrips and arbitary embeds in Sites’ as they’re ‘too powerful a phishing vector’.
However, he notes the email is ‘much more sophisticated’.
So, how did Johnson spot it was dodgy?


The white space is reportedly a clue something’s phishy (Twitter/ @nicksdjohnson)
How to spot a phishing email
Johnson points out the ‘first clues’ come with the header of the email.
“Although it was signed by http://accounts.google.com, it was emailed by http://privateemail.com, and sent to ‘me@blah,'” he states.
And the ‘second clue’? “Below the phishing message is a lot of whitespace (mostly not shown) followed by ‘Google Legal Support was granted access to your Google Account’ and the odd me@… email address again,” Johnson flags.
Johnson notes he’s submitted a bug report to Google, later updating Google responded saying it ‘will be fixing the oauth bug’.
What Google has said about the ‘no-reply’ email
A spokesperson from Google told UNILAD: “We’re aware of this class of targeted attack from this threat actor and have rolled out protections to shut down this avenue for abuse. In the meantime, we encourage users to adopt two-factor authentication and passkeys, which provide strong protection against these kinds of phishing campaigns.”
Featured Image Credit: Getty Images/Chesnot
Topics: Google, Technology, Twitter


The FBI has issued an urgent warning to three billion Google Chrome users over a new dangerous hacking scam.
It’s no secret that surfing the web and even using our phones can put us in danger of hackers.
From dodgy fake WiFi networks to scamming apps, intruders are constantly trying to find new ways to manipulate technology to gain our data and personal information.
Now, the federal agency is warning cybercriminals have created yet another method, this time by making new websites on Google to convert one type of file into another, like a .doc file to a .pdf file, or for MP3 or MP4 files, which are instead warped with malicious code.
Once the sham files are downloaded, cybercriminals are reportedly gaining access to users’ stored information, like social security numbers, passwords and banking.


Some three billion users could be at risk (Getty Images)
Vikki Migoya, public affairs specialist for FBI Denver, said: “Unfortunately, many victims don’t realize they have been infected by malware until it’s too late, and their computer is infected with ransomware or their identity has been stolen,” reports The Daily Mail.
Migoya added: “The scammers try to mimic URLs that are legit – so changing just one letter, or ‘INC’ instead of ‘CO.’
“Users who in the past would type ‘free online file converter’ into a search engine are vulnerable, as the algorithms used for results now often include paid results, which might be scams.”
The FBI is now advising people who use the internet browser Chrome not to download file converters from unfamiliar websites.
If you do download one and realize you are a victim of the scam, the agency says to contact your bank or financial institution ‘immediately,’ report the incident to IC3.gov. and get your device checked out.


Hackers are constantly coming up with new ways (Getty Images)
It added: “Run up-to-date virus scan software to check for potentially malicious software installed by the scammers.”
“Consider taking your computer to a professional company specializing in virus and malware removal services.”
The news comes as millions of Google Chrome users were also warned about 16 different types of browser extensions that had been comprised by hackers.
The list of extensions being impacted include Blipshot, Emojis, Color Changer for YouTube, Video Effects for YouTube and Audio Enhancer, Themes for Chrome and YouTube Picture in Picture and Mike Adblock for Chrome, Super Dark Mode and Emoji Keyboard Emojis for Chrome.
Adblock for Chrome, Nimble Capture, KProxy and Page Refresh, Wistia Video Downloader, Adblocker for Chrome and Adblock for You are also said to be influenced by hackers.
GitLab Threat Intelligence, which discovered the dodgy scheme, stated on its website: “We identified a cluster of at least 16 malicious Chrome extensions used to inject code into browsers to facilitate advertising and search engine optimization fraud.
“The extensions span diverse functionality including screen capture, ad blocking and emoji keyboards and impact at least 3.2 million users.
“The threat actor uses a complex multistage attack to degrade the security of users’ browsers and then inject content, traversing browser security boundaries and hiding malicious code outside of extensions. We have only been able to partly reproduce the threat actor’s attack chain.”
While Google confirmed to UNILAD that the ‘extensions are removed from the Chrome Webs store,’ the tech pros said people who have downloaded them already will need to manually delete them from their devices.
Featured Image Credit: Chesnot/Getty Images
Topics: Google, Technology, World News


The FBI has warned people who use Google’s Gmail about a dangerous ransomware scheme.
More than 1.8 billion people could be at risk from hackers who hold your private data hostage if you make this one easy mistake.
The infamous Medusa ransomware group has committed a slew of victims across its criminal career, and has already victimized over 300 targets via email scams.
These phishing scams go on to exploit unprotected software and they can then take over whatever information they wish and use it.


The FBI has warned Gmail users (Mateusz Slodkowski/SOPA Images/LightRocket via Getty Images)
Because of how widespread this issue is, the FBI and US Cybersecurity and Infrastructure Security Agency (CISA), has shared how devastating the scheme is for critical infrastructure sectors.
They’ll target employees in hospitals, schools, and major businesses.
So, how can you prevent yourself from being targeted?
Well, Medusa is able to take data by sneaking into computers after tricking unsuspecting victims with fake emails or by locating weak spots in their systems via malicious online content.
This could be fake links which seem like real sites, but are actually going to hack you as soon as you click on it.
As soon as you’re in the trap, your important files will be locked and inaccessible, and then copied for the hackers to ransack.
Medusa will then send ransom for the data, which can be thousands or millions of dollars.
If you don’t pay up, they might leak your information to the public, or simply refuse to unlock the files.
This is why the FBI and CISA have urged Gmail users to set up two-factor authentication (2FA).


The agency gave prevention tips (Getty Stock Image)
If you haven’t used 2FA, it’s essentially a security measure which forces you to create a pin or key for access, or it’ll send a code to your email address for you to enter to the window before allowing you access.
The agency also state that you should make sure that your software is up to date, and that if you have sensitive information on your devices, keep multiple copies on separate servers or hard drives.
For large organizations, CISA has suggested they prevent unknown or untrusted origins from accessing remote services.
Checking who has special administrative powers and limiting what they can do to is also one of the tips or splitting their computer networks into smaller sections to prevent Medusa from spreading into all areas.
The ransomware-as-a-service group create the malicious software and are career criminals.
Also, if you are sent a link, do not open it if you were not expecting it.
This warning comes after federal agents raised the alarm over a new scam that involves a phone call and smart tech trickery which many iPhone and Android users struggle to recognize as a scam.
This scam pretends it’s a technical support line, a bank, the US Customs and Border Protection (CBP) or even your local police force.
It can be quite convincing as the scammers have been able to ‘spoof’ the caller ID number.
So, if you think your convincing customer support call is a scam, just hang up.
Featured Image Credit: Getty Images/NurPhoto
Topics: Google, Technology, US News, Crime


Google has commenced its plan to delete inactive Gmail accounts, sending warning messages to those that may be affected.
Toward the end of 2023, the company revealed that it would be deleting Gmail accounts that hadn’t been used in more than two years.
For an account to be considered inactive, users must not have been logged into it via any of Google‘s services like Gmail or Google Photos.


Inactive Gmail accounts will be deleted by Google. (Chesnot/Getty Images)
VP of Product Management at Google Ruth Kricheli explained last year: “If an account hasn’t been used for an extended period of time, it is more likely to be compromised.”
She went on to explain that these measures are necessary to ‘protect our users from security threats like spam, phishing scams, and account hijacking.’
Internal analysis by Google found that old accounts are far more likely to be compromised due to having out-of-date or re-used passwords and are ten times less likely to have two-factor authentication set up.


Inactive accounts are far more at risk of security threats. (Thiago Prudencio/SOPA Images/LightRocket via Getty Images)
“These accounts are often vulnerable, and once an account is compromised, it can be used for anything from identity theft to a vector for unwanted or even malicious content like spam,” Kricheli noted.
Google is sending warning emails to users before the deletion of their accounts takes place.
A reporter for Forbes, Davey Winder, shared that he received a warning message in January this year that a Google account he had not used in eight months was going to be deleted on September 20 if he didn’t take action.
While Google and Gmail have been asking users to check old accounts to see if they received a similar warning, they should not be a huge cause for concern if you want to keep your account as there are three simple steps you can take to keep it active.


There are three steps you can take to ensure your account’s safety. (S3studio/Getty Images)
The first is to read or send an email on the account to give Gmail a flag that you’re still there and using it. So go ahead and type up some random email to one of your friends.
The second is to share a photo or watch a YouTube video while signed into the Google account you want to keep.
The third is to use Google Drive or Google Search while signed onto the account. Basically, any little thing to show that this account is still being used by you for Google products.
Per Forbes, doing any of these three steps at least once a year should be able to ensure that your account is safe from being deleted.
Featured Image Credit: Getty/SOPA Images/Getty/Willie B. Thomas
Topics: Google, Technology


Apple has urged users to update their iOS after identifying two ‘extremely sophisticated attacks’.
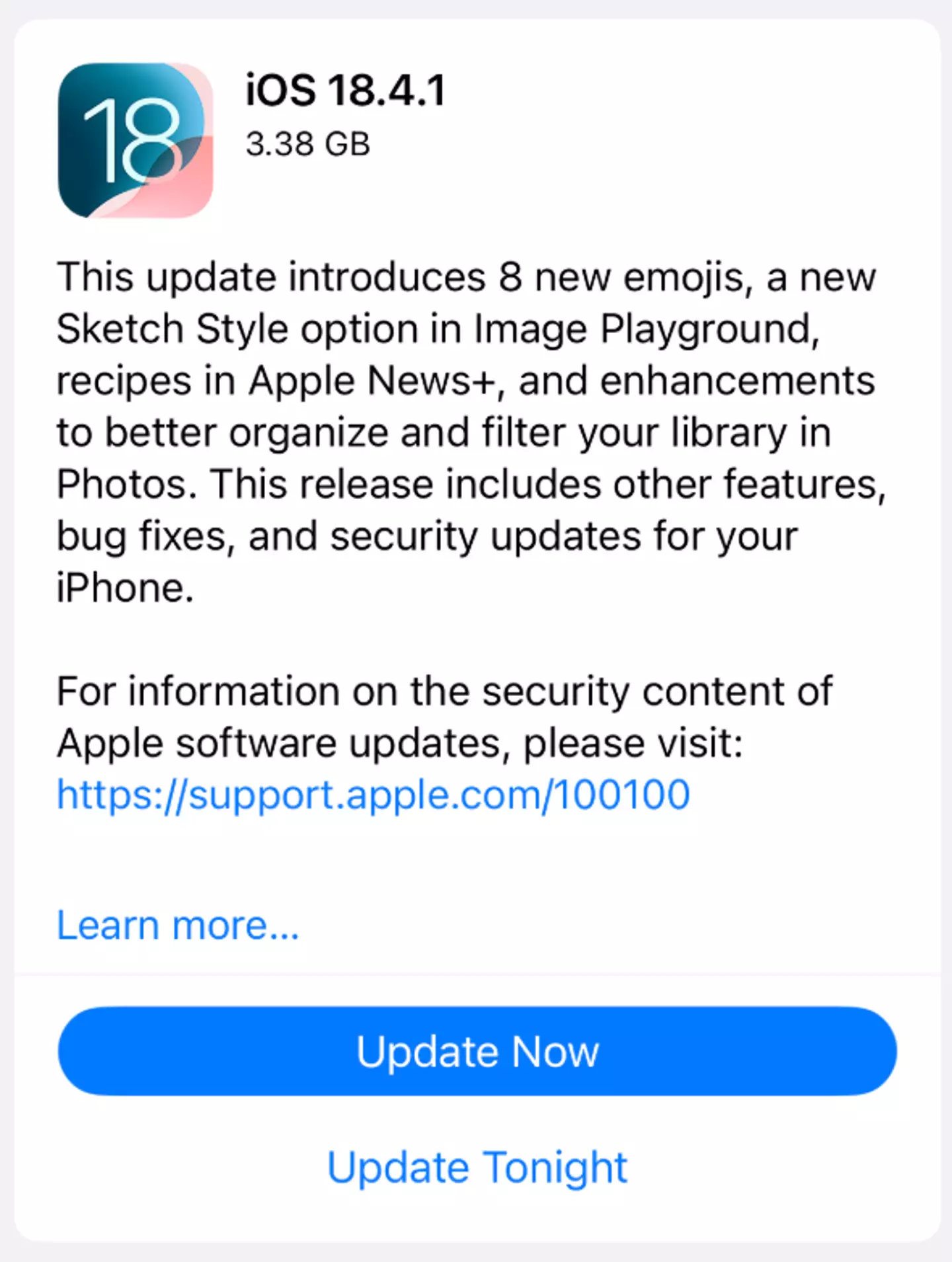
Apple revealed the latest iOS update in a post to its website yesterday (April 16). If you’ve already noticed the Software Update available on your phone, you’ll have seen a small description about iOS 18.4.1
Softening the blow slightly before diving into the nitty gritty, the update for iOS 18.4.1. reads: “This update introduces eight new emojis, a new Sketch Style option in Image Playground, recipes in Apple News+ and enhancements to better organise and filter your library in Photos.
“This release includes other features, bug fixes and security updates for your iPhone.
Granted, emojis and new Sketch Style options are great and all that, but if you’re a bit more concerned about the ‘bug fixes and security updates’, then don’t fret because we did some deep-diving for you.
What’s included in Apple’s iOS 18.4.1 update
On it’s website’s page titled ‘About the security content of iOS 18.4.1 and iPadOS 18.4.1’, Apple notes: “For our customers’ protection, Apple doesn’t disclose, discuss, or confirm security issues until an investigation has occurred and patches or releases are available. Recent releases are listed on the Apple security releases page.”
Thankfully, the investigation has occurred and problems have been identified.
Apple’s report continues identifying two iPhone security flaws which the iOS 18.4.1 update will better protect users against.
But what are they?

Apple’s iOS 18.4.1 update (Apple)
What the two iPhone security flaws are which Apple’s iOS 18.4.1 update is fixing
Well, Apple’s site details the two security flaws as being to do with its CoreAudio and RPAC components – to do with memory corruption issue.
CoreAudio is ‘available for: iPhone XS and later, iPad Pro 13-inch, iPad Pro 13.9-inch 3rd generation and later, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 7th generation and later, and iPad mini 5th generation and later’.
The attack on the CoreAudio is detailed by Apple as being ‘an extremely sophisticated attack against against specific targeted individuals on iOS’ and could see ‘code execution’ occur if an audio stream is processed in a ‘maliciously crafted media file’.
RPAC is ‘available for: iPhone XS and later, iPad Pro 13-inch, iPad Pro 13.9-inch 3rd generation and later, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 7th generation and later, and iPad mini 5th generation and later’.
Apple details it discovered an attacker ‘with arbitrary read and write capability may be able to bypass Pointer Authentication’.
“Apple is aware of a report that this issue may have been exploited in an extremely sophisticated attack against specific targeted individuals on iOS,” it reiterated.


It’s worth updating your iPhone just in case (Jakub Porzycki/NurPhoto via Getty Images)
How Apple’s iOS 18.4.1 has resolved the security issues
Thankfully, iOS 18.4.1 has resolved both issues, Apple noting the ‘memory corruption issue’ with CoreAudio was ‘addressed with improved bounds checking’ and the RPAC issue was ‘addressed by removing the vulnerable code’.




